You might have heard of the recent ransomware attacks worldwide by ‘WannaCry’ which locked out many users out of their computers and asked for a Bitcoin equivalent to $300. However, it looks like it was just the beginning of a series of cyber attacks. The WannaCry or WannaCrypt ransomware attack affected more than 230,000 computers in over 150 countries, with the NHS, Spanish phone company Telefónica and German state railways among those hardest hit. What’s Next? Heard of Petya ransomware yet? Let us start from the very beginning.
What is Ransomware?
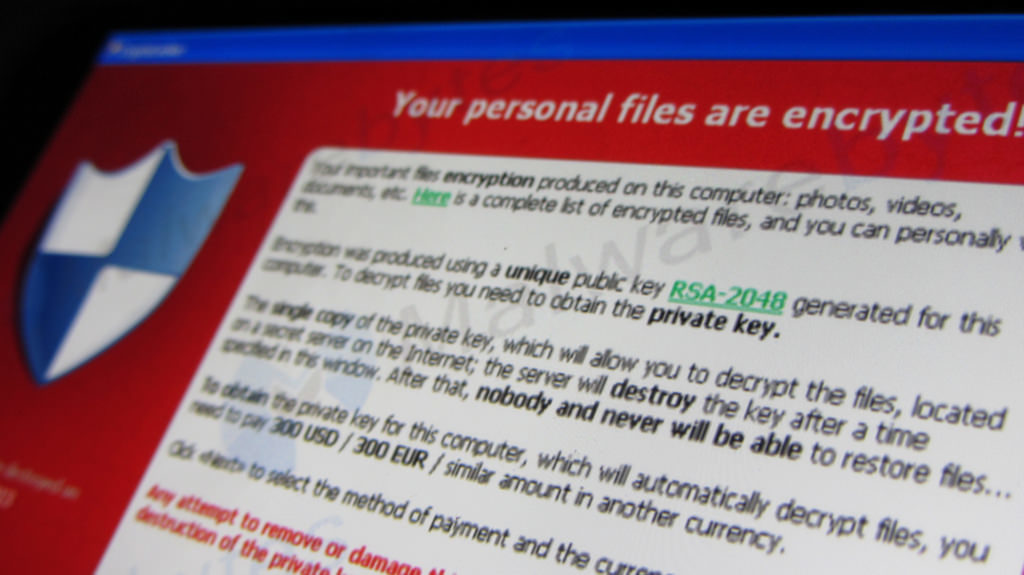
Ransomware is a type of malware that blocks access to a computer or its data and demands money to release it.
How does it work?
Ransomware encrypts important documents and files and then demands a ransom in Bitcoin, for a digital key needed to unlock the files. If victims don’t have a recent back-up of the files they must either pay the ransom or face losing all of their files.
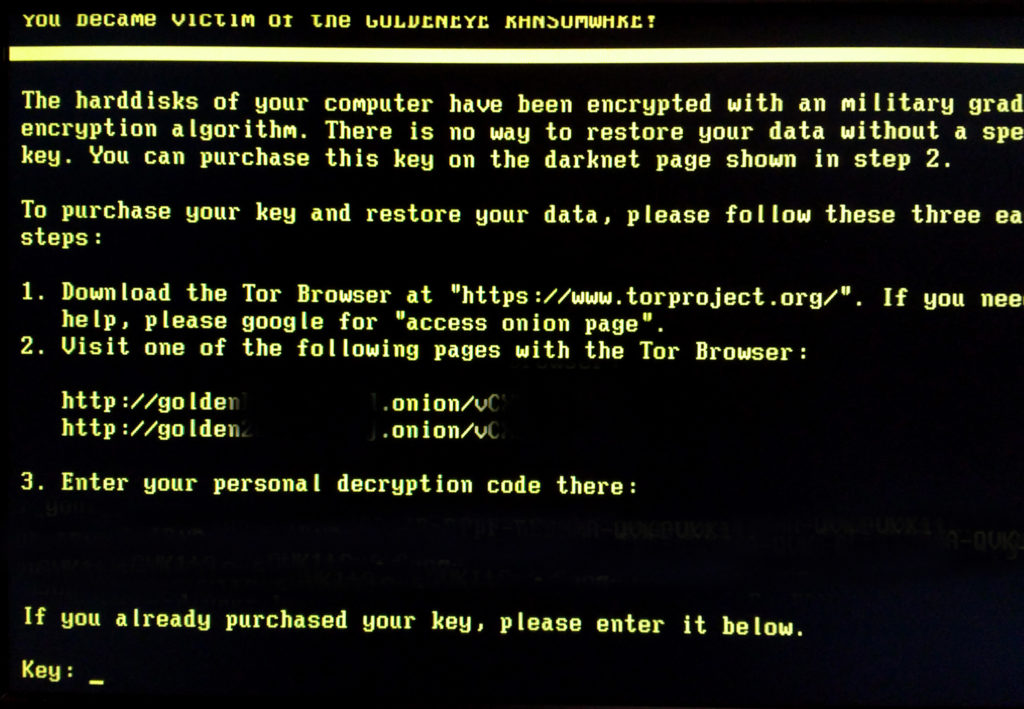
What is Petya ransomware?
According to Wikipedia “Petya” is a family of encrypting ransomware that was first discovered in 2016. The malware targets Microsoft Windows-based systems, infecting the master boot record to execute a payload that encrypts the NTFS file table, demanding a payment in Bitcoin in order to regain access to the system.”
Petya was first discovered in March 2016, which propagated via infected e-mail attachments. The new variant propagates via the EternalBlue exploit, which is generally believed to have been developed by the U.S. National Security Agency (NSA), and was used earlier in the year by the WannaCry ransomware. Although it purports to be ransomware, this variant was modified so that it is unable to actually revert its own changes.”
Although it is not the same ransomware, this variant of Petya ransomware was modified to be more lethal than WannaCry. This variant was modified so that it is unable to revert its own changes.
It’s worse than WannaCry, it’s wiper pretending to be ransomware.
Where did it start?
Security researchers and Ukraine’s cyber police are pointing fingers at MeDoc, a third-party accounting software product, used by many industries in Ukraine including financial institutions. MeDoc pushed out an update which was then compromised by hackers. When this was installed, computer networks got this malware. The second wave of infections was circulated by a phishing campaign featuring malware-laden attachments.
Why is it called “Petya”?
This malware appears to have a similar code as an older piece of ransomware that really was called Petya. But hours after the outbreak security researchers noticed that the code has been modified. Researchers at Russia’s Kaspersky Lab redubbed the malware NotPetya. On top of that, other researchers who independently spotted the malware gave it other names: Romanian’s Bitdefender called it Goldeneye, for instance.

Who has been hit?
Microsoft estimates over 12,000 machines have been hit by the cyber attack. Reports suggest that the malware has spread across the U.S., large parts of Europe, South America, and big countries in Asia too.
Major corporations have also been affected including WPP, Maersk, Russian oil giant Rosneft, and public and private institutions in Ukraine.
WPP said that it has taken steps to contain the attack with the priority now to return to normal operations. Many of the businesses under the WPP brand were affected but they are “experiencing no or minimal disruption.”
Maersk said that IT systems were down across multiple sites and some business units, but the issues have been contained. It is now working on a “technical recovery plan”. The impact on the business is still being assessed.
Russia, which was one of the countries hit, said the cyber attack caused no serious problems at either a state or corporate level in the country.
Who did it?
It is not clear, but it seems likely it is someone who wants the malware to pretend as ransomware, while actually just being destructive, particularly to the Ukrainian government. Security researchers noted that the real Petya ransomware was designed to make money while this one was designed to spread fast and cause damage.
Are you at risk?
So far, major businesses have been attacked. You will know if you have been infected as a screen will appear demanding payment of $300 in Bitcoin to unlock the file. Researchers have warned against paying the ransom because the email now associated with the hackers has been decommissioned, meaning even if you pay, there is no way to contact the criminals.
If your organization is running a vulnerable version of Windows that hasn’t patched (updated with the latest fix) then your business could be at risk.
How to protect yourself?
Individuals and small businesses should:
- Run Windows Update to get the latest software updates.
- Make sure any anti-virus product is up to date and scan your computer for any malicious programs. It’s also worth setting up regular auto-scans.
- Back up important data on your computer so it can be recovered if it’s held for ransom.
Large organizations should:
- Apply the latest Microsoft security patches for this particular flaw.
- Back up key data.
- Scan all outgoing and incoming emails for malicious attachments.
- Ensure anti-virus programs are up to date and conducting regular scans.
- Make sure to run “penetration tests” against your network’s security, no less than once a year, according to the Department of Homeland Security.
Have any questions about Petya Ransomware?
Ask us in the comments below.



